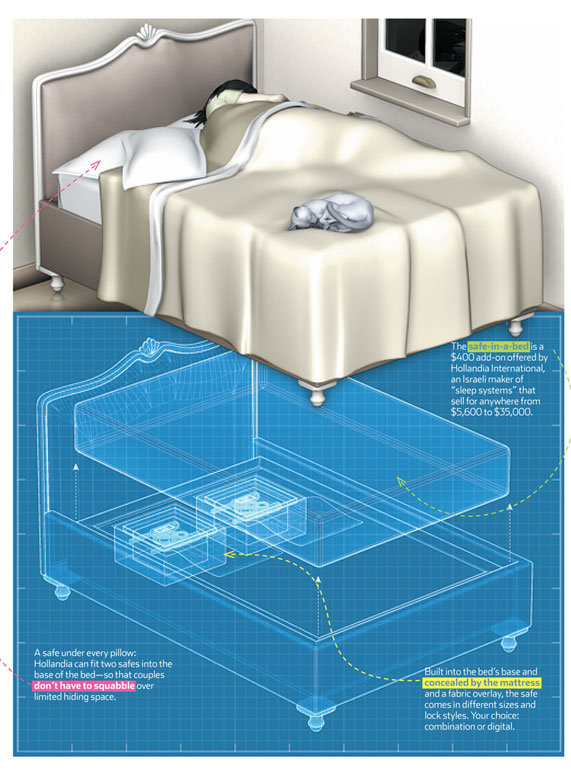
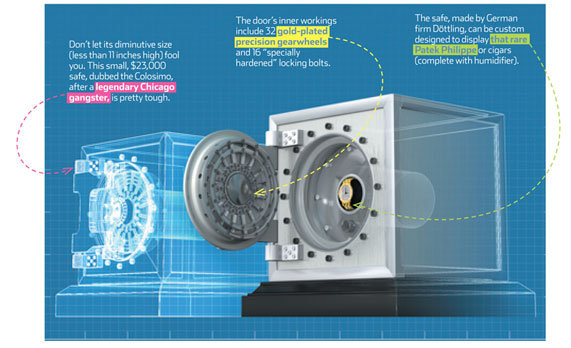
Thank you to Karen for sending this in...
Please Take The Time To Watch This.....
IT IS IMPORTANT TO YOUR FINANCIAL SECURITY....
We have also added some books and resources at the bottom that you can check out to protect you and your loved ones. As we have discussed on prior calls, you can also use aluminum foil. Be Aware......