Below is some information that may help you too. With Christmas coming up, it only gets worse.
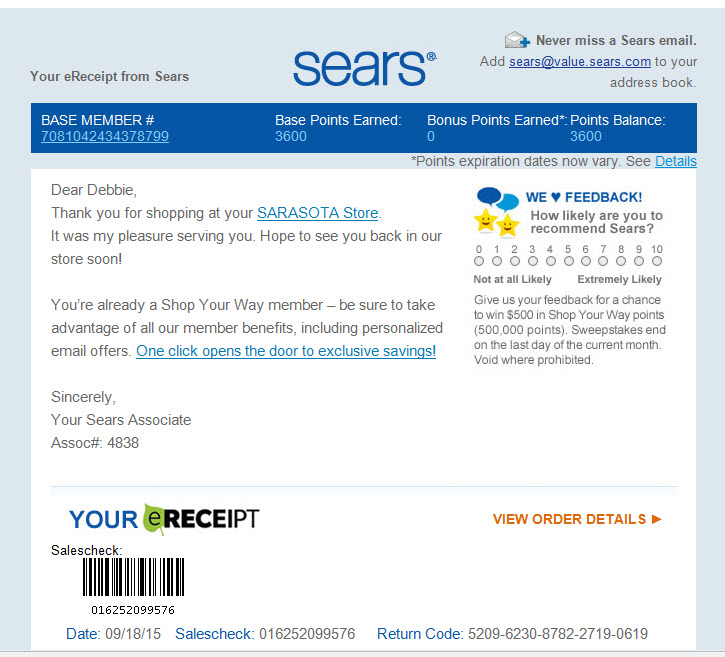
I recd this email last night that looks pretty legitimate - purchase at Sears store where I live for $359.00 - since I was not at the store and dont go there very often I knew it was not us - so I was not sure whether someone was scamming me OR maybe they set up an account in my name and charged this. Mainly because my Business was a victim of Identity Theft (that is a whole story in itself) under the email address they sent to me. A good way to tell if your emails are scam is below
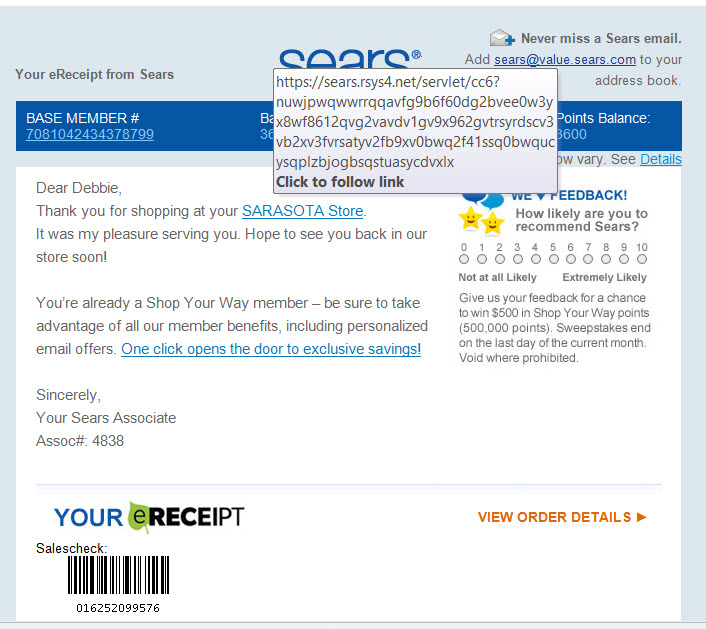
#2 If you take your mouse and HOVER over one of the links and it is not who it is coming from IT IS A SCAM. In my case, since it was coming from Sears it should have been SEARS.COM
In the case below it is SEASR.RSYS4.NET Guys that is Russia
It is a total scam. Delete the email and do not click on anything.
Scam Detectors
Receipt invoice scam
How the scam works:
(with video below) You receive an e-mail from a big chain store that you purchase groceries from on a regular basis (eg. Walmart, Superstore, etc). “We are now happy to offer online your last receipt. Please find it attached to this e-mail. Thank you for shopping with us”.
Most likely the attachment will be a Zip. file, that will contain a virus, keystroke logger, or malware. Look at the domain name of the sender’s e-mail. Is it the store’s name.com or does it have extra letters and numbers (bestbuy.com or bestbuy529a5.com)?
Wtach the video below to see en explanation of this scam, as featured in the news.
Receipts Sent by Email Scam Video Below
How to avoid:
Never open attachments from unknown senders.
Make your friends and family aware of this scam by sharing it.
Dont fall for email scams
Phishing emails try to get you to click on links that take you to fake websites - or open attachments that will do bad things. Look out for the telltale signs of a scam email.
Amazon Book Link for Computer Security
Hope that helps someone out there NOT lose everything on their computer.
Have an incredible day